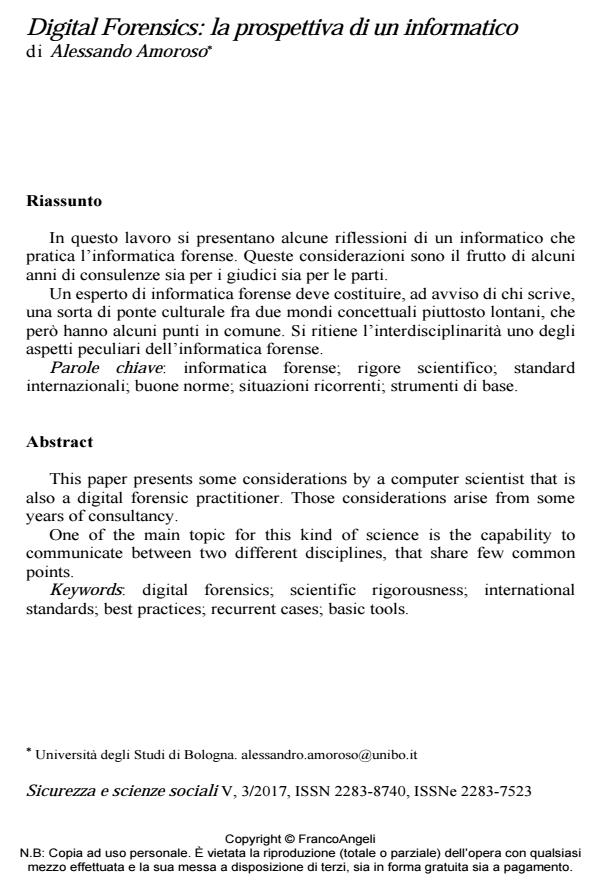
Digital Forensics: la prospettiva di un informatico
Journal title SICUREZZA E SCIENZE SOCIALI
Author/s Alessando Amoroso
Publishing Year 2018 Issue 2017/3
Language Italian Pages 17 P. 110-126 File size 228 KB
DOI 10.3280/SISS2017-003010
DOI is like a bar code for intellectual property: to have more infomation
click here
Below, you can see the article first page
If you want to buy this article in PDF format, you can do it, following the instructions to buy download credits
FrancoAngeli is member of Publishers International Linking Association, Inc (PILA), a not-for-profit association which run the CrossRef service enabling links to and from online scholarly content.
This paper presents some considerations by a computer scientist that is also a digital forensic practitioner. Those considerations arise from some years of consultancy. One of the main topic for this kind of science is the capability to communicate between two different disciplines, that share few common points.
Keywords: Digital forensics; scientific rigorousness; international standards; best practices; recurrent cases; basic tools.
Alessando Amoroso, Digital Forensics: la prospettiva di un informatico in "SICUREZZA E SCIENZE SOCIALI" 3/2017, pp 110-126, DOI: 10.3280/SISS2017-003010